What is 2FA (two-factor authentication)?
 The two-factor authentication method is an authentication process that requires an additional authentication step in addition to having a strong password like a push notification, a security question, or a SMS code sent to a trusted device.
The two-factor authentication method is an authentication process that requires an additional authentication step in addition to having a strong password like a push notification, a security question, or a SMS code sent to a trusted device.
Customers use the internet to sign up for social media accounts like Facebook, create an email account, apply for car loans, log into their doctor’s patient portal to make appointments, even stream the game on Sunday. Whatever you’re doing online these days, there’s a good chance you need a user account and a strong password to do it. However, even with a complicated password, your personal information and online accounts are still at risk. Why? Because electronic fraud and hacking are at an all-time high. Data breaches are now a matter of “when" not “if.”
Sophisticated passwords increase protection against brute force attacks, but long strings of letters, characters and numbers aren’t necessarily enough to help you sleep at night. Plus, if you’re using the same credentials for multiple accounts, the consequences of a breach and unauthorized access to your online account are even greater, not to mention potentially expensive and time-consuming to repair. To address the liability of protecting online identities and guarding personal data, cybersecurity experts recommend multi-factor authentication, which is a type of authentication that requires two or more factors of authentication.
Two-factor authentication, or 2FA for short, requires a password (the first factor) then a second factor like a numeric code, push notification, security question, security token or a biometric such as a fingerprint or facial recognition (the second factor) from an authenticator app to access online data. Also known as two-step verification or dual-factor authentication, the 2FA authentication process validates both sets of user credentials before granting access to an online account.
Download PYMNTS new report - - Authenticating identities in the digital economy
Most 2FA processes combine two of five common authentication factors: knowledge; possession; inheritance; location, and time. Knowledge factors are items the user knows such as a password or PIN, whereas a possession factor is something the user possesses, such as their mobile phone or an ID. Another second factor used is known as Inheritance factors, also known as biometric factors, include fingerprints, voice tone and other inherited identifiers, such as facial recognition. If you are using your fingerprint or facial recognition on your mobile device, then you are using a biometric authentication.
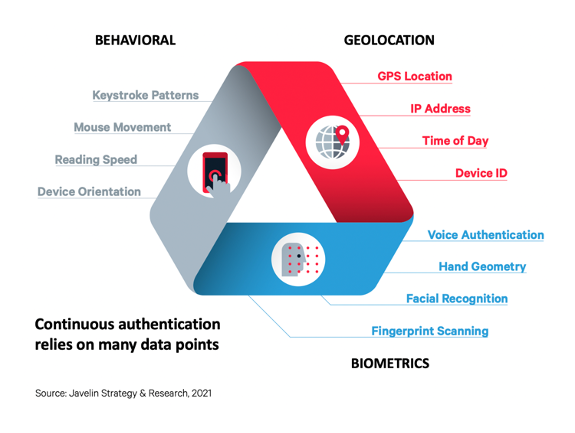 As the name suggests, location factors come from data sources such as IP addresses or GPS software with verifiable location-specific information. Last, but equally valuable in the 2FA toolbox, are time factors where user authentication only occurs during fixed periods and prohibits access outside of these timeframes.
As the name suggests, location factors come from data sources such as IP addresses or GPS software with verifiable location-specific information. Last, but equally valuable in the 2FA toolbox, are time factors where user authentication only occurs during fixed periods and prohibits access outside of these timeframes.
Consumers will likely recognize knowledge, possession, and inheritance factors as the most common 2FA methods from personal experience. However, even though 2FA is familiar, internet users still seem less concerned about password theft than ease of access. Opening their email fast or checking a bank balance as quickly as possible is seemingly more important than securing their online accounts.
Is 2FA enough?
According to Verizon’s 2019 Data Breach Investigations report, companies in every industry are at risk of a breach even with an additional authentication process. “Regardless of the type or amount of your organization’s data, there is someone out there who is trying to steal it.” Record-setting data thefts at Adobe, Anthem, eBay, Equifax, Home Depot, Hilton, Hyatt, JP Morgan Chase, LinkedIn, Marriott International, Sony Pictures, Target, Uber, the United States Office of Personnel Management, and Yahoo prove if you’re online, your personal information is in jeopardy. Considering the 2019 was the worst year for data breaches on record, it seems 2FA isn’t automatically enough to protect your virtual identity, bank account, or credit score.
As an affordable, typically user-friendly process, 2FA minimizes the possibility of online threats such as synthetic identity fraud, account takeover fraud, hacking, and phishing. Still, like any system, 2FA is only as strong as the weakest link.
Watch this video on layered identity and continuous authentication from Javelin's Tracey Kitten
It's about using the right two factors
Two-factor authentication systems can be vulnerable, unless you use the right combination of factors. Methods that rely on security tokens depend on manufacturer quality, and processes using biometric factors need reliable, secure software as well. A two-factor authentication process built on knowledge factors, such as one-time verification code sent to the user’s mobile device, are susceptible to social engineering hacks. “Any 13-year-old could download the tool and actually carry out these attacks,” says Kevin Mitnick, once one of the FBI’s most wanted hacker. (Read more about authentication and fraud in Javelin's new report, Consumer preference drives shift in authentication) And research suggests increasing cybersecurity in the C-suite is a smart idea. In 2018, “C-level executives were 12 times more likely to be the target of social incidents and nine times more likely to be the target of social breaches than in years past. Security incidents and data breaches that compromised executives rose from single digits to dozens" as reported by Verizon. No security system is perfect; hackers can intercept 2FA SMS codes and texts as efficiently as they crack weak passwords. When you use the right two factors, like ID document verification hand-in-hand with a biometrics verification you're ensuring a more layered and more secure approach.