Mitek’s digital manipulation detection tackles the rise of AI-generated fake ids
The democratization of fraud
In the past, producing a convincing fake ID required specialized skills, costly equipment, or collaboration with professional forgers. Today, however, underground platforms such as OnlyFake and VerifTools have “democratized” the creation of fraudulent documents by harnessing generative AI. For as little as $15, anyone can quickly generate a near-authentic passport, driver’s license, or national ID—sometimes in bulk quantities. This ease of access has shattered the skill barrier to fraud, allowing even low-level criminals to produce highly convincing forgeries.
Scaled production and ‘Fraud-as-a-Service’
Because these platforms automate much of the ID creation process, perpetrators can scale their operations dramatically. Some services can generate thousands of unique documents per day by merely uploading a spreadsheet of personal data and images—often gleaned from data breaches or social media. It can also be noted that these services allow the generation of not only IDs, driver's licenses, and passports but also bank checks, social security cards, credit cards, military IDs, and more. This “mass production” approach fuels synthetic identity fraud, account takeovers, and other forms of financial crime on a global scale.
Evolving tactics
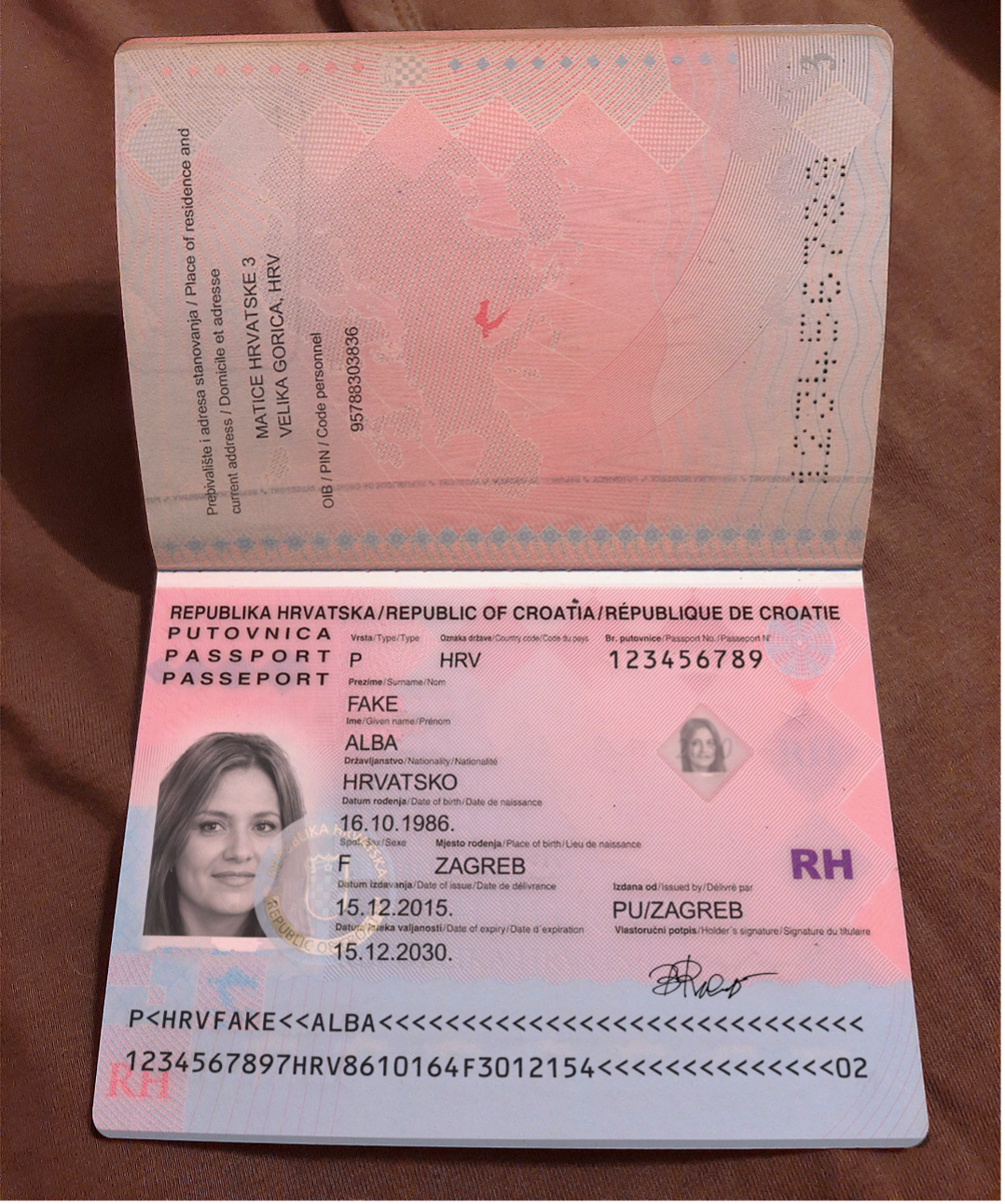
Beyond standard ID templates, these fraud platforms are integrating sophisticated elements, such as:
- Simulated holograms and watermarks to mimic official security features
- Machine-Readable Zones (MRZs) and barcodes that match the visible information
- AI-generated portraits or stolen profile photos, seamlessly inserted onto the document.
- Perforations that match the visible standards
- AI-generated signatures that match the biodata
Coupled with print-and-cutout attacks (like printing a digital image on a high-quality paper to mimic a “physical” ID) and deepfake-based liveness spoofs, this new wave of Fraud-as-a-Service is overwhelming existing identity checks.
Figure 1. Example of an AI-Generated Passport. This passport image—created using a VerifTools-like service—illustrates how AI-based tools can replicate design elements, security features, and personalized data with alarming realism.
Implications for financial institutions
For banks, fintechs, and other organizations reliant on remote identity verification, the result is a sharp uptick in fraud attempts—and a heightened risk of onboarding malicious actors. Manual reviews or legacy verification technologies often fail to spot the microscopic digital artifacts these AI tools leave behind. Meanwhile, compliance risks rise as institutions inadvertently onboard bad actors who can now pass superficial KYC controls. This dual threat—scaled production plus advanced forgery—places unprecedented pressure on risk teams to adapt quickly.
Mitek’s digital manipulation detection: a targeted defense for AI automated document fraud detection
To counter the explosive growth of AI-assisted forgeries, Mitek’s Verified Identity Platform (MiVIP) now incorporates a specialized layer of digital manipulation prevention —purpose-built for AI automated document fraud detection in today’s threat landscape. Engineered to address the exact challenges posed by OnlyFake-like services, this feature uses machine learning models to analyze ID images for telltale signs of digital manipulation.
High-level overview
- Seamless integration: Digital manipulation detection operates within MiVIP’s orchestration layer, working automatically whenever a document is submitted. It layers on top of standard ID checks and biometric verifications without adding friction to the user flow.
- AI-powered forensic analysis: A suite of ensemble neural networks examines each pixel for compression artifacts, mismatched textures, and repeated patterns commonly produced by generative AI tools.
- Contextual verification: The system cross-references data fields (like birthdates, addresses) with recognized formats and real ID reference libraries, spotting improbable or illogical alignments.
How the feature works
Mitek’s digital manipulation detection is a formidable tool for spotting manipulated documents, because it is powered by an ensemble of advanced deep learning models that are trained on a massive, continuously evolving dataset of both genuine IDs and known AI-forged documents. Instead of dividing the process into separate, specialized modules, the ensemble leverages the cutting-edge neural network architectures to collectively learn to recognize distinct patterns that generative AI and other manipulation techniques tend to leave behind. By exposing the models to thousands of examples of each attack type—from simple text overlays to highly sophisticated deepfake composites—the system refines its ability to spot anomalies that traditional AI automated document fraud detection methods often miss.

Figure 2. Example of the same signature detected on different fake passports.
During analysis, the ensemble flags a range of typical artifacts found in synthetic and manipulated IDs, such as:
- Morphological and compression artifacts
- Tiny distortions or irregular pixel clustering introduced by generative AI or repeated image saves.
- Color channel discrepancies
- Subtle mismatches in RGB or YCbCr channels that suggest artificial blending or overlay.
- Background inconsistencies
- Incongruous transitions between a face photo and the ID’s background, or awkward merging of text fields and underlying color gradients.
- Unique signatures and data points
- Identical signatures, holograms, watermarks, or microtext repeated across different documents generated by the same forgery service (see Fig 2).
- Layer and sharpness mismatches
- Differences in edge clarity or crispness where a new headshot or text has been “pasted” on top of an original template (see Fig 3).

Figure 3. Example sharpness difference – letter F is sharper than the other elements of the document.
By aggregating the detection results and assigning a risk score, the system quickly determines whether the document is likely genuine or exhibits patterns indicative of AI-driven manipulation. This comprehensive, data-driven approach ensures our document manipulation detection maintains robust defenses against emerging forgery methods, while continuously learning from new fraudulent samples encountered in the field.
Layered approach against AI-generated documents
While our digital manipulation detection capabilities focus on catching digitally altered documents, they integrate tightly with other Mitek defenses:
- Screen replay detection
- Recognizes when a user is photographing a screen-based ID instead of a physical document (an “image-of-image” attack).
- Captures environmental cues like screen glare or display pixel patterns.
- Portrait substitution detection
- Ensures the person in the ID photo matches the selfie or live video feed.
- Prevents criminals from simply swapping in a stolen or AI-generated headshot digitally or physically
- Printed cutout detection
- Identifies attempts to print a digital fake and present it as a physical ID.
- Looks for paper edges, inconsistent texture, or unusual glare/lighting.
The synergy among these features allows Mitek to address all major variants of AI-driven ID fraud—whether the fraudster is uploading a purely synthetic document or physically presenting a printed counterfeit.
Coverage matrix
Below is an example matrix summarizing how Mitek’s layered approach addresses different types of AI-automate- document fraud. Each detection method contributes differently depending on the attack vector:
- High: The detection method is specifically tuned for this attack vector, providing robust and reliable coverage.
- Medium: The detection method can flag certain indicators of this attack vector but may need support from other checks for full coverage.
- Low: The detection method offers minimal or incidental coverage, as it is not primarily designed to detect this type of attack.
|
Attack Vector |
Digital Manipulation Detection |
Screen Replay Detection |
Portrait Substitution Detection |
Printed Cutout Detection |
|
AI-Generated ID Image (Uploaded) |
High – Spots digital artifacts, suspicious layering |
Medium – Checks metadata, suspicious re-uploads |
Low – (Only relevant if user attempts portrait match) |
Low – (No physical presentation) |
|
Screen Presentation of the AI-Generated ID |
Medium – If digitally manipulated |
High – Detects screen glare, pixel patterns |
Medium – Face mismatch can trigger follow-up |
Low – (Not printed) |
|
Deepfake Portrait Substitution of the Original ID |
Medium – May show artificial layering |
Low – Not always triggered if doc is purely digital |
High – inconsistency of the edges of the inserted photo |
Low – (No printing) |
|
Printed Cutout of AI Fake ID |
Medium – Some digital artifacts might remain visible |
Medium – Could detect scanning artifacts |
Low – (If same face used for selfie) |
High – Paper edges, inconsistent texture flagged |
By combining these defenses, Mitek’s platform is designed to make it significantly harder for AI-generated forgeries to evade detection. The net effect is a substantial reduction in fraud attempts slipping through automated systems.
Future outlook & ongoing innovation
Digital manipulation detection has been shown to significantly reduce forgery-based fraud compared to traditional ID checks, thanks to its robust ensemble modeling. This solution and its continuous improvements are built upon three key pillars:
- Continuous adaption - The system constantly learns from fraud samples—both discovered in the field and generated in-house—rapidly adjusting to new tactics deployed by document generation services. This feedback loop ensures detection accuracy continually improves over time.
- Template-agnostic approach - Rather than relying on rigid templates, our system leverages the artificial neural networks that analyze the entire document image with no requirements to “know” document template or positions of digital signatures, holograms, and security elements. This allows it to handle an ever-growing range of ID formats with no re-engineering, a critical advantage for a global client base.
- Adaptive risk policies - As regulations evolve, and fraudsters shift their methods, Mitek’s modular design lets clients dynamically adjust risk thresholds, escalate cases to forensic experts, or incorporate additional biometric checks—striking an optimal balance between user experience and security.

